Testing wireless IoT on the bench

Analysing the network activities of wireless devices can provide important information about security gaps.
Currently more headline than reality, the Internet of Things (IoT) will soon permeate everyday life through home automation, wearables and connected car technology. It will ultimately have a far greater impact than smartphones do today.
An increasing number of devices are being designed with integrated wireless modules in order to exchange (often sensitive) data, transmit measured values and remotely control systems. The number of ‘things’ communicating via the internet is expected to increase drastically over the coming years, with a major surge predicted after 2020 when 5G provides the necessary network resources (Figure 1).
The downside of this development is that every wireless device with an IT core becomes a potential target for hackers.
The cyber eavesdropping methods recently made public by WikiLeaks have made this threat tangible. Every IoT-connected device represents a potential risk, especially in light of the fact that IoT components are (currently) generally more poorly protected than products originally designed for the IT world.

For reasons ranging from price and time pressure to lack of awareness and technical expertise, the security features in many wireless products in which IT plays a secondary or non-existent role (eg, household appliances) are rudimentary and poorly implemented.
Along with absent or weak encryption, open ports (communications channels) and vulnerable firmware, installed apps represent a significant security risk if developers fail to adhere to common IP connection security standards or do not provide regular updates.
A single weak point can provide a loophole enabling unauthorised access to one or many devices. A widespread compromised IoT device can create difficulties for network operators and even cause networks to crash.
Enterprises at risk
While IoT is still in its infancy, classic wireless communications is omnipresent and extensively used in both professional and personal environments. This becomes a problem for companies when these two spheres intermingle, eg, when employers follow the ‘bring your own device’ motto and personal mobile devices are used for business purposes.
Unfortunately, it must be assumed that attackers will attempt to exploit any and all security gaps. Not only operating systems, but the increasing number of apps harbour a security risk. The multitude of helpers found on any well-stocked personal mobile phone increase the probability of a poorly programmed or outdated app revealing a security gap. In the worst case, an entire corporate network can be accessed via such a device.
Devices become truly susceptible to threats when jailbreaking or rooting manipulates their operating systems and deactivates fundamental security functions. But for attackers, looking for loopholes in allegedly secure original operating systems is a better alternative since there are only two major systems (Android and iOS) in use worldwide.
New test methods needed
It must be determined whether a mobile device is at risk and whether the installed apps meet security requirements. The task of the responsible IT team is to verify that any wireless device used in the corporate environment safeguards the confidentiality and integrity of the data it stores and transmits, irrespective of whether it uses WLAN or a cellular connection (it cannot be assumed that malware will behave the same in both environments).
In the past, this task was easier to describe than perform since the communications behaviour of the devices could not be readily examined. An analysis of the servers contacted on the internet, and especially their location, provides essential information about unwanted communications. The server location can be identified using IP geolocation as long as no obfuscation techniques have been used.
Any abnormality must be further examined and, if required, the source apps should be banned from devices used within the company. Apps developed specifically for company use, however, must certifiably behave as expected, especially with respect to security.
Security parameters revealed
The Rhode & Schwarz CMW500 wideband radio communication tester can help developers improve the security of IP-based data communications for mobile devices and IoT modules. The new IP connection security analysis reporting module (CMW-KM052) performs real-time IP data traffic analysis in a controlled test environment (Figure 2).

The CMW500 also emulates a mobile network or WLAN access point. The data application unit (DAU) is required for security analysis. It provides the device under test (DUT) with IP addresses and manages the connection with servers on the web. The CMW-KM052 analyses and logs the security-related parameters of the data traffic. This enables developers to detect and close security gaps early in the design process. It gives IT personnel a tool to determine whether mobile devices used for business purposes comply with internal security policies.
The analysis software produces real-time statistics of the IP connections and communications protocols used. The software module makes it possible to search for sensitive information in data streams, including for user-specified input such as passwords and device IMSIs. If this information is transmitted unencrypted, the software lists the target address, domain name and, if possible, the source app. The module also analyses SSL/TLS handshake parameters as well as certificates and country/domain names of the server location.
The SSL/TLS handshake that the client and server use to agree on the cryptographic method is essential for a secure connection and is therefore closely examined. The CMW-KM052 displays the cryptographic methods (cipher suites) offered by the client during call set-up as well as the cipher suite chosen by the server, including key lengths and other parameters. The CMW-KM052 can even analyse the certificate transmitted by the server.
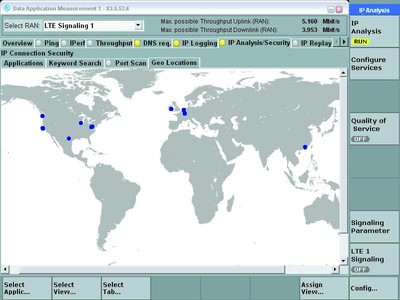
When analysing communications behaviour, one of the most important things users want to know is where the involved servers are located (country). Geolocation makes it possible to determine this information. Since IP domains are unique and registered, localisation is successful 95–99% of the time. Domain names provide additional security-related information. The new analysis option enables users to easily detect suspicious domains and unwanted countries that might present a security problem (Figure 3).
The port scan function is another important security feature of the software. The client and server of an application talk to one another via ports. Via the operating system, an application offering a service in a network (server) opens a port (address) that the client can access. This port waits for inquiries in the ‘listen’ state. A port in this state that is unintentionally open to the internet is a potential gateway for attackers.
Malware such as Trojans often open back doors via freely accessible ports (some ports are reserved for certain applications). This is why it is highly recommended to review the open ports in a system from time to time — an easy-to-implement measure with the CMW-KM052 option.
No additional software is required on the DUT to use the analysis tool. The tests are independent of its operating system. DUTs with an antenna connector can be connected to the CMW500 via a cable. DUTs without a connector can be accommodated in an RF-shielded box from Rohde & Schwarz and connected to the CMW500 via an air interface (Figure 4).

Summary
Until now, it has been very difficult to analyse data traffic from mobile and IoT devices. Security weak points could go undiscovered for long periods of time. The CMW500 wideband radio communication tester with the CMW-KM052 analysis option tackles this problem. Users can obtain a detailed overview of security-relevant communications parameters in a freely configurable controlled wireless environment and also determine whether a device behaves differently in WLAN and cellular networks.
Developers can detect security gaps early in the design process. IT teams can analyse the communications behaviour of smartphones, tablets and apps used in the corporate environment. Automotive OEMs and network operators can verify that connected car and IoT devices comply with the specified connection security standards.
The test sequence is very simple since the DUT requires no preparation. The CMW-KM052 option integrates seamlessly into the powerful CMW500 test suite. A single test and measurement instrument now enables RF analysis in cellular and non-cellular networks, protocol tests and IP application tests, as well as analysis of security-relevant parameters for IP data communications.
Achieve accurate RF measurements by understanding spectral purity
Selecting a signal generator with high spectral purity ensures that the measurements signify the...
Signal generators: does analog or digital make a difference?
With so many options, it's important to understand which signal generator is best to achieve...
Using AI to build your next-gen wireless system
The central challenge engineers face when designing wireless systems and networks is their...




